The Definitive Google Workspace Admin guide to Manage Windows Devices
AN ADMIN GUIDE TO MANAGE WINDOWS DEVICES VIA GOOGLE
- Google recently launched an option for Google Workspace (and Cloud Identity) customers to manage Windows 10 devices right from Google Admin Console.
- I invested sometime in learning how it works, so I can help community manage Windows devices via Google Workspace and get more out of their investment in Google.
- Let me share everything I learnt, and hopefully it would help you seamlessly manage your Windows 10 devices as a Google Workspace or Cloud Identity Administrator.
Google Workspace Windows Management Overview
I certainly agree that each prominent operating system in the market today (e.g Windows, Mac, ChromeOS, or Linux) can get the job done, and it essentially is a matter of personal preference based on what works best for you.
I switched from Windows to Mac back in 2013 and never looked back, however some of my friends & colleagues love the Windows operating system and I respect their choice.
Instead of imposing, smart organizations prefer to provide their users with a choice and let them decide what make them more productive, this might be the reason vendors like Google & Microsoft are also investing in interoperability along with building their ecosystem.
As an example, Microsoft allows organizations to manage their android devices via intune, and Google also provides an option to manage devices from other vendors.
Microsoft of course provides a way to manage Windows devices, but won’t it be better if Google provides that option to Google Workspace customers and let you get more out of your investment in Google (especially if you either do not use Active Directory or have plans to replace it with Google Directory)?
Drum roll…….It is time for some good news:)
Google indeed recently launched an option where Google Workspace customers like you would be able to manage Windows 10 devices right from Google Workspace or Google Cloud Identity Admin Console.
This new Windows device management functionality works seamlessly with your Active Directory too, and just in case if you are fortunate to get rid of Active Directory, then even better, you can still manage your Windows devices from the Google admin console.
In this blog post, we will cover things in great detail and hopefully it should help you understand how windows devices management via Google works, and how you can set it up in your environment.
Let us first start with understanding what exactly I mean when i say “Manage Windows devices via Google Workspace”
Well, essentially 3 things
1. Authenticate to Windows via Google Workspace : It offers an authentication method where your users should be able to login to Windows 10 devices via their Google Workspace or Google Cloud Identity credentials.
2. Windows devices Inventory : It offers an easy to manage inventory management system where all your connected Windows devices can be seen in your Google Workspace Admin console along with some metadata like last sync time, OS version, and an option to block, delete or wipe these devices.
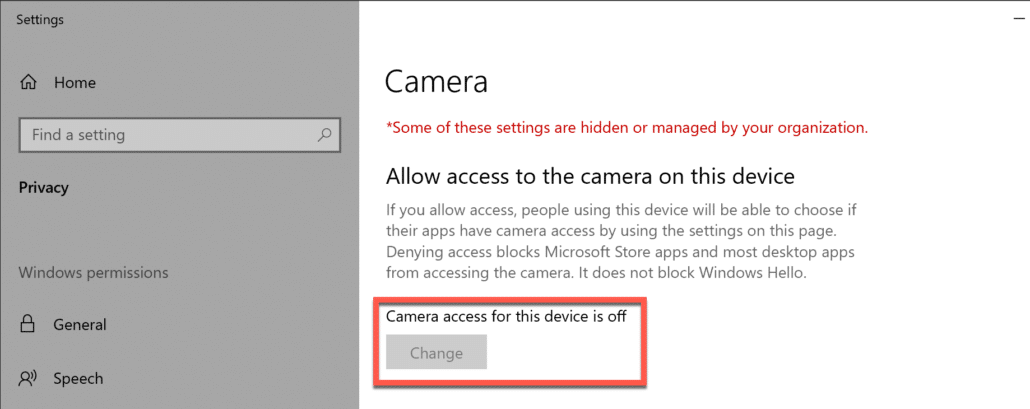
3. Windows devices management : It allows to manage Windows settings on enrolled devices, you may think of it like pushing your GPO policies right from your Google Workspace or Google Cloud Identity admin console (e.g enable camera, disable USB etc).
Manage Windows 10 devices via Google – Terminology :
Google calls this “Enhanced Desktop Security for Windows”, which has two modules-:
- Google Credential Provider for Windows (GCPW) : It is an installable utility that you install on users windows devices (either manually or via app distribution) to let them sign in on Windows via their Google account. It is available to all Google Workspace and Cloud Identity plans.
- Windows Device Management : It allows pushing policies to Windows 10 devices (e.g manage windows updates, enable camera, disable USB etc) which is only available in selective Google Workspace and Google Cloud Identity plans (more details about it are provided in system requirements section).
Benefits of managing your Windows devices via Google Workspace or Google Cloud Identity :
Security : You should be able to push security policies (e.g disable camera, usb etc) along with option to sign users out or wipe data from their Windows devices.
As your users would be able to login to windows 10 devices via their Google credentials, you can also enforce multi factor authentication (MFA) for secure login.
Rich user experience : Once your users sign in to windows devices via their Google credentials, a session is established, which helps them to login to any Google Workspace (e.g Gmail, Drive) or assigned SAML application (e.g Salesforce) without a need to enter credentials again.
Your users will not need to remember different sets of credentials (e.g for Windows, for Google Workspace, for 3rd party applications), just login to Windows via Google Workspace or Google Cloud Identity once, then login to any assigned applications via Single Sign on (SSO).
Updates management : You should be able to control how and when your users get Microsoft windows device security updates.
Increased ROI : Till the time you have supported Google Workspace or Google Cloud Identity subscription, you do not need any additional license specifically for managing your windows devices via Google.
Now, with this context, let us understand how Google Workspace provides your Windows users rich login experience and let you seamlessly manage their windows devices.
Windows Authentication & Management via Google Workspace
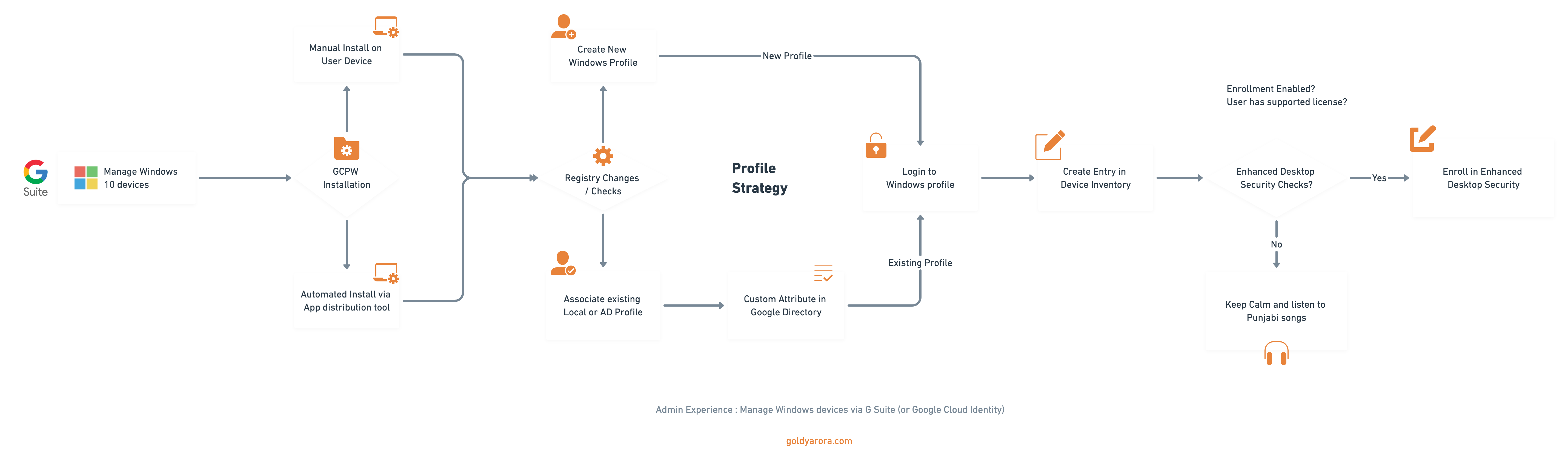
I have put some flowcharts below which would help you understand it better, but here is the summarized version of how managing Windows devices via Google works.
Google offers a utility called Google Credential Provider for Windows (GCPW) which you install on your users Windows devices either manually or via your preferred application distribution tool (PowerShell script is included later in this post).
This utility (along with a few registry changes) does a few things-:
- At the time of GCPW installation on Windows devices, you tell Google to either associate Google account with your existing Windows profile (e.g local or AD profile) or create a new Windows profile.
- After GCPW installation on Windows devices, users sign in with their Google Workspace account password, GCPW then either create and login to a new Windows profile or to an existing one based on your configuration.
- Though Internet connection is required for the first login via Google to sync Google password to Windows (and to push custom settings if you have those in place), but subsequent logins should work fine even without internet access (unless Google session expired or password is changed) because now essentially their Windows password is same as Google Workspace.
Password Synchronization :
This also requires us to keep our Google Workspace and Windows password in sync. There are couple of options available for you to keep these passwords in sync, lets explore them-:
- If your windows user changes his/her Google Workspace password, then this new password should be synchronized with Windows at next login via Google Workspace (however user should be connected to internet for this).
if the user logs in offline mode after changing his/her Google Workspace password, then old password should be entered to login to Windows as GCPW didn’t get a chance to push updated password (due to being offline). - If your user changes password on Windows for the Windows local profile, then GCPW would detect and push this changed password securely to Google Workspace.
- However, if your user has an Active directory managed Windows profile, and change the password, then user would either need to change the Google Workspace password manually (make it same as Windows).
You may consider utilizing Google Workspace Password Sync (GSPS) utility offered by Google, which detects AD password changes and automatically push them to Google Workspace (via Directory API) to keep them in sync.
Note : Your Google Workspace or Cloud Identity password policy should be same (or stronger) than Active Directory or Windows password requirements.
Windows User Login Experience
Login to Windows via Google Workspace - User Experience
Before we start required setup to let your users login to their Windows devices via Google Workspace, let us explore user experience-:
- Non-Domain joined machines -: Users would either click on existing Windows tile, or “Add Work Account”
- Domain joined machines : Users would either click on their existing windows tile OR Other Accounts on their Windows devices.
- Above is configurable as we’ll see later in the post based on whether you want Google to create new windows profile or associate with local or AD profile.
- Your users would then be shown an option to sign in via Google where they’ll enter user email, password (and second authentication factor if you have enforced it).
- Based on your (configurable) profile strategy Google Credential Provider for Windows (GCPW) would either create new Windows profile or associate it with existing local or AD windows profile.
Note -: After successful authentication, GCPW looks for a custom attribute and its value (e.g SamAccountName for AD, and un:Windows username for local windows profile) in Google Workspace directory, if found, it then checks if a Windows profile exists for this user and finally associates Google Workspace account with this profile, otherwise it creates a new windows profile for Google Workspace user. - Once the user logins to Windows (either new or existing profile), this device will be enrolled in GCPW, and you should be able to see it (along with metadata) under device inventory in Google Workspace admin console.
- If you have supported Google Workspace or Google Cloud Identity subscription and you have not disabled auto enrollment via registry changes (cover later in this post) , then these devices would be automatically enrolled in Enhanced Desktop Security, so you can push policies to them.
Login to Windows via Google Workspace - Behind the scenes

Windows Devices Management Prerequisites
System Requirements for managing Windows 10 devices via Google Workspace (or Google Cloud Identity)
1. Supported Google Workspace or Google Cloud Identity Subscription
GCPW (which includes login via Google, SSO to Google and SAML Apps, and windows devices inventory) is available to all Google Workspace & Cloud Identity subscriptions, however Windows management (e.g pushing custom settings / policies) is included in specific plans, following table should be helpful to understand it.
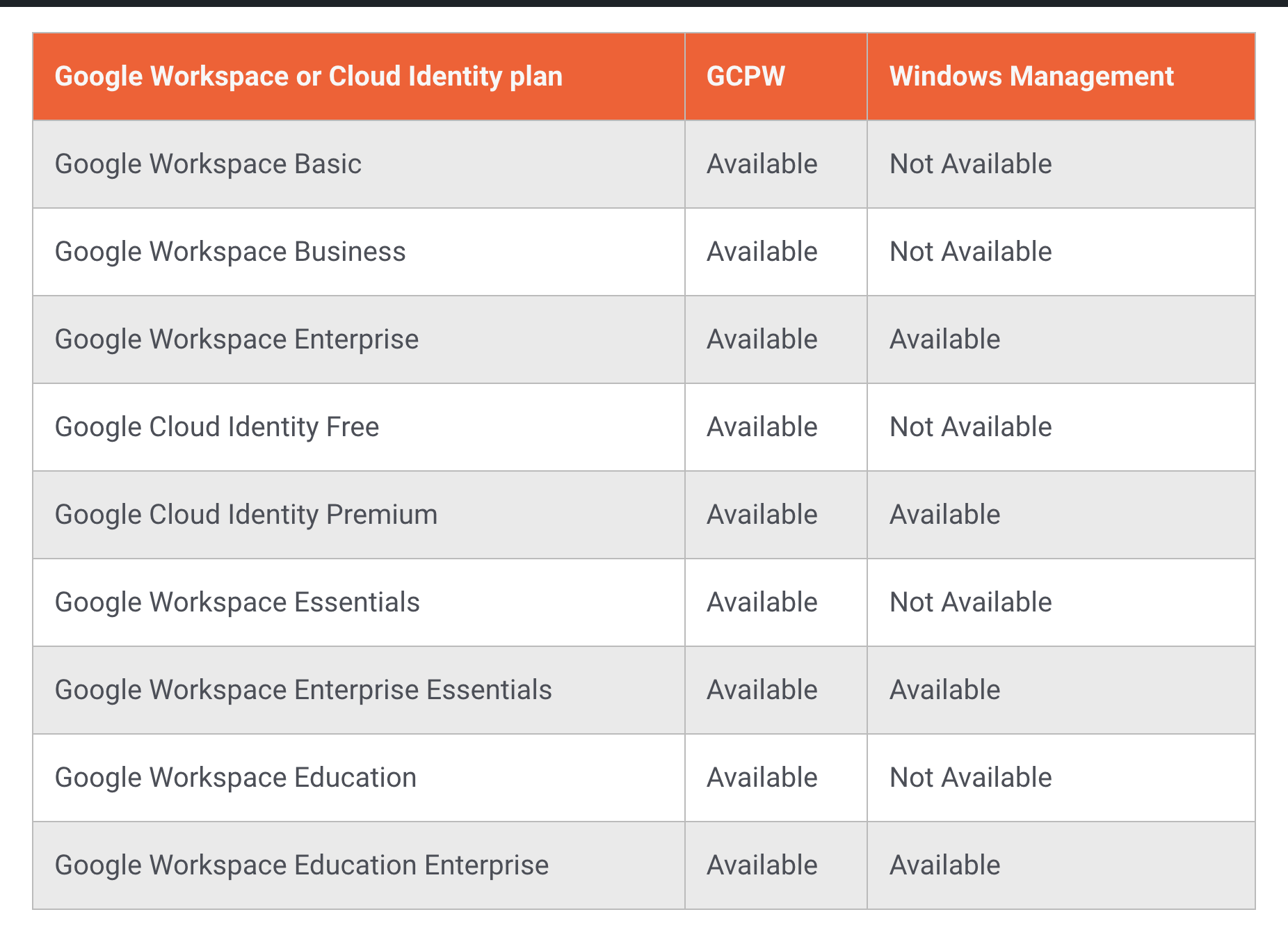
Note : For Windows management (e.g pushing policies to user devices), each user should have a supported Google Workspace or Google Cloud license.
2. Supported Windows 10 Version
— You would need version 1803 or newer for Windows 10 Pro, Pro for Workstations, Enterprise, or Education.
3. Supported Google Chrome (for GCPW)
— You would need Chrome Browser 81 or later.
4. Local Administration Rights & enough storage
— Local system admin rights to install Google Credential Provider for Windows (GCPW) on Windows devices if you are doing manual install on user devices (You can also deploy the installer via your app distribution tool).
— Google also recommends 100 MB available disk space for Google Chrome and 3 MB for GCPW.
Here is the reference PowerShell script provided by Google which downloads GCPW and configures the required registry to restrict sign in to Windows devices from provided domains only, simple hover on the script and it’ll give an option to copy it.
Windows Management via Google Workspace Setup
Manage Windows devices via Google Workspace (Admin Workflow)
Step # 1
Enable Enhanced Desktop Security & apply policies
Let us start with enabling enhanced desktop security and applying a few policies to our Windows devices.
Note -: If you do not meet requirements for “Enhanced Desktop Security” as mentioned above, OR if you only want to setup Google Credential Provider for Windows (authentication) so your users can login via Google Workspace, then you can skip this step and go to Step 2 of the setup.
In my case, I use Google Workspace Enterprise, and prefer to automatically enroll my windows devices to enhanced desktop security, and also apply a few policies on my users first Windows login via Google Workspace.
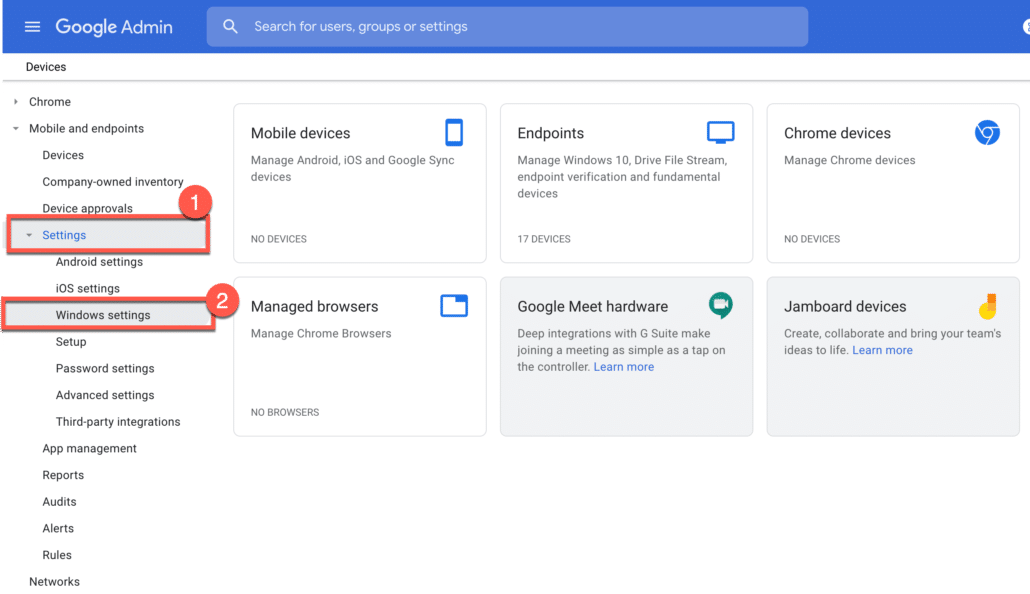
So, I will login to Google Workspace Admin Console, and go to Devices as shown below.

If you have supported Google Workspace or Google Cloud Identity subscription, you would see “Windows Settings” under Settings section as shown in below screenshot. Click on “Windows Settings” in this section.
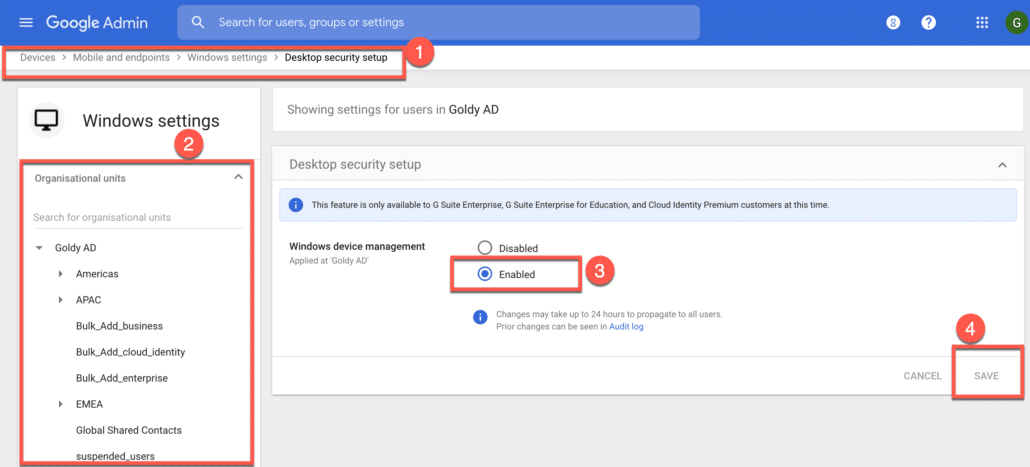
Here you can enable “Enhanced Desktop Security” or device management on either the root organization (which means all users) or selective child organization units (which means it’ll apply only to the users who belong to these child org units).
Click on save changes.
Step # 2:
Apply custom settings for Windows 10 devices
This is only available in Enhanced Desktop Security, you may refer to system requirements above to see which Google Workspace and Cloud Identity plans offer it.
As per Microsoft “Windows 10 custom profiles use Open Mobile Alliance Uniform Resource Identifier (OMA-URI) settings to configure different features. These settings are typically used by mobile device manufacturers to control features on the device”.
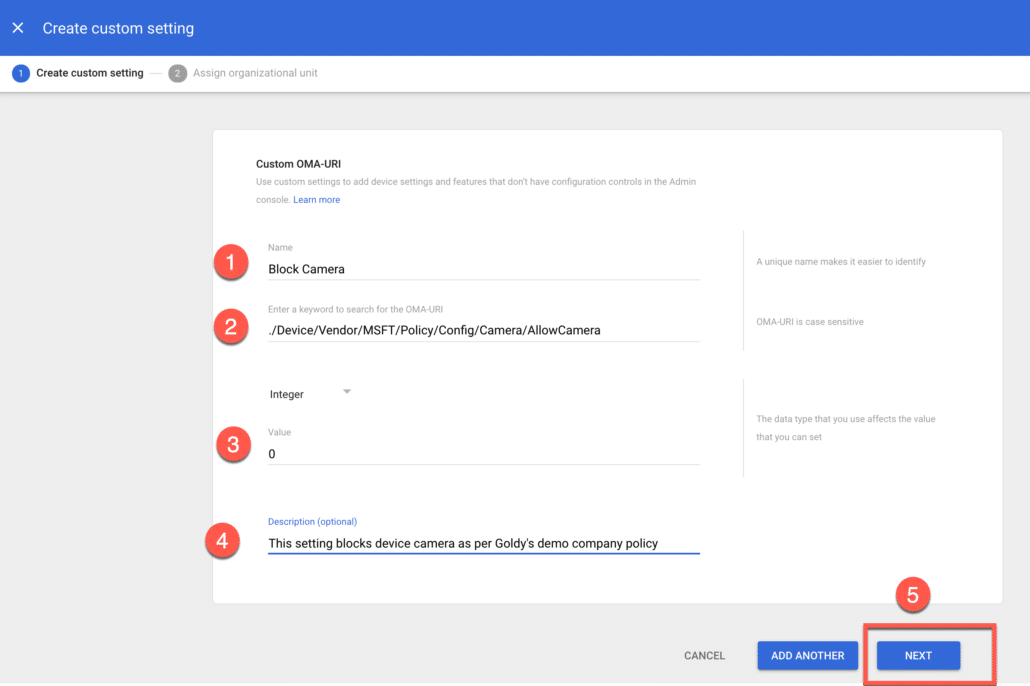
Google provides you option to apply custom settings to your Windows 10 devices via OMA-URI where essentially you put the URI for a specific policy (e.g Allow Camera) and then enter its value (e.g 0 to disable camera, 1 to enable camera).
Let us create a simple policy of restricting our Windows users to use camera on device.
In your Google Workspace or Google Cloud Identity Admin Console, go to device management, click on Windows settings (as shown in the screenshot above) and then click on custom settings.
You would see your existing custom policies here, I do not have one yet, so i’ll click on “Add a custom setting” to create one.
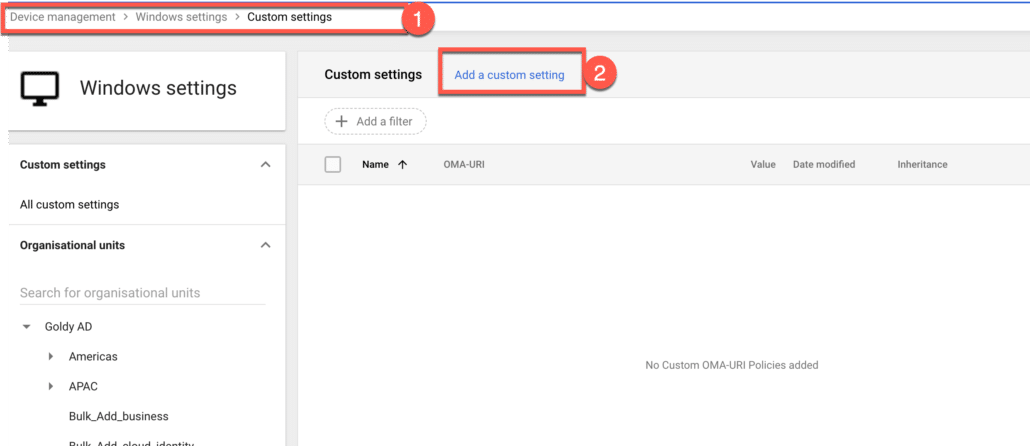
Though you can find a list of OMA-URIs on Microsoft’s site, but Google also let you easily search while creating them in Google Workspace Admin console.
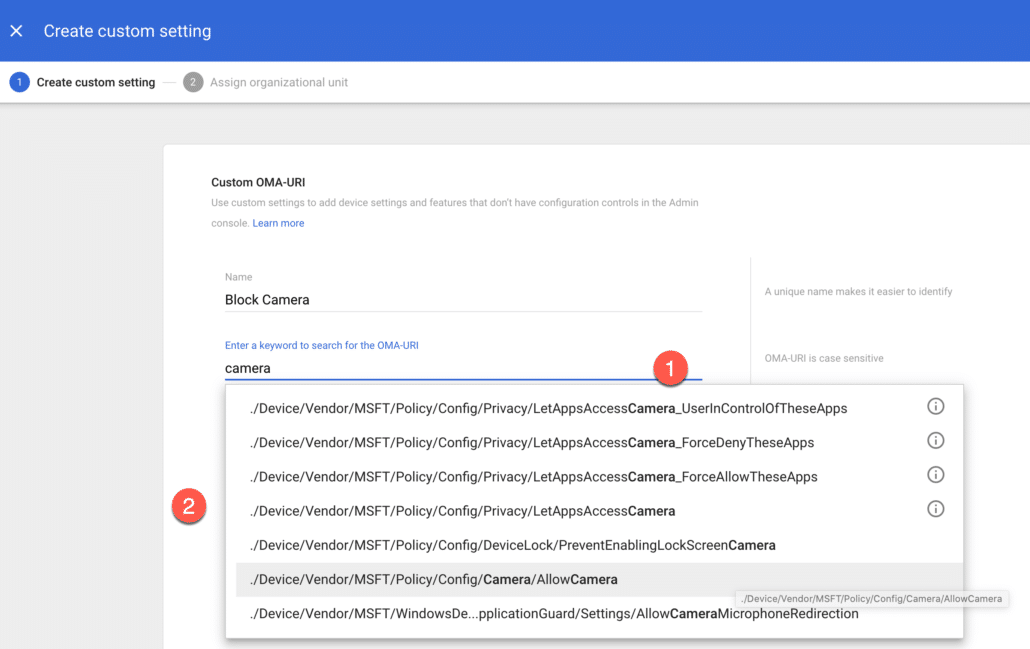
I will search for “Camera” to see associated custom policies option, and then select the one which allows or block camera usage (as shown in the screenshot below).
Your OMA-URI based custom setting policy would look like this, once configured click on Next.
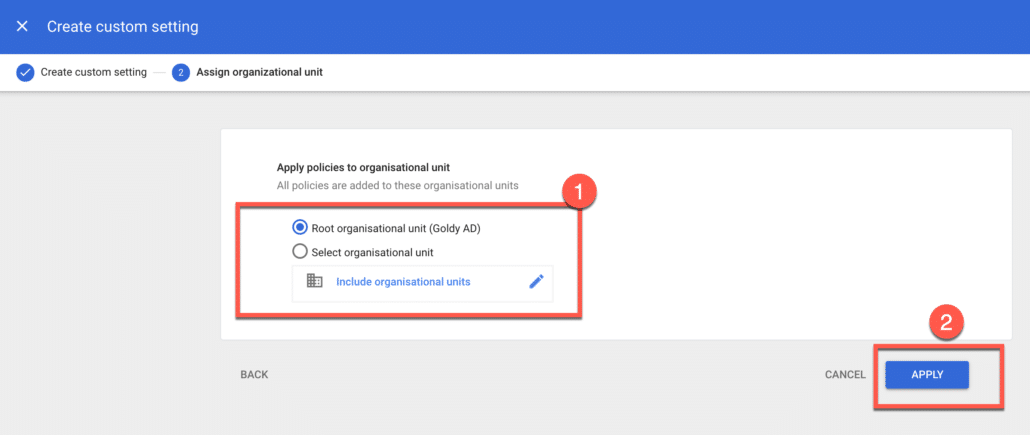
Here you have the flexibility to define the scope for this custom policy, you can either apply it to all users by selecting your root organizational unit OR you can go granular by selecting child organizational units so it only applies to users who belong to child org units.
Now, ideally, when my Windows user login via Google Workspace credentials, camera will not be available to use, and user will not be able to enable it.
Additional Steps - Depending on your profile strategy.
I want Google to create a new Windows profile when my users login to Windows via their Google Workspace or Google Cloud Identity credentials, however if you want, you can also associate their existing Windows local or Active directory profile with Google account.
You should follow either of the following steps only if want to associate users’ Google account with local or AD windows profile, otherwise skip them.
Additional Step : If you want to associate existing Windows AD profile with Google
In this post, I will be configure Google to create a new windows profile with my users Google credentials, however if you want to rather associate your users Google profile with existing Windows Active Directory Profile, then you should perform this additional setup.
1. Login to your Google Admin console –> go to Users –> click on Manage Custom Attributes
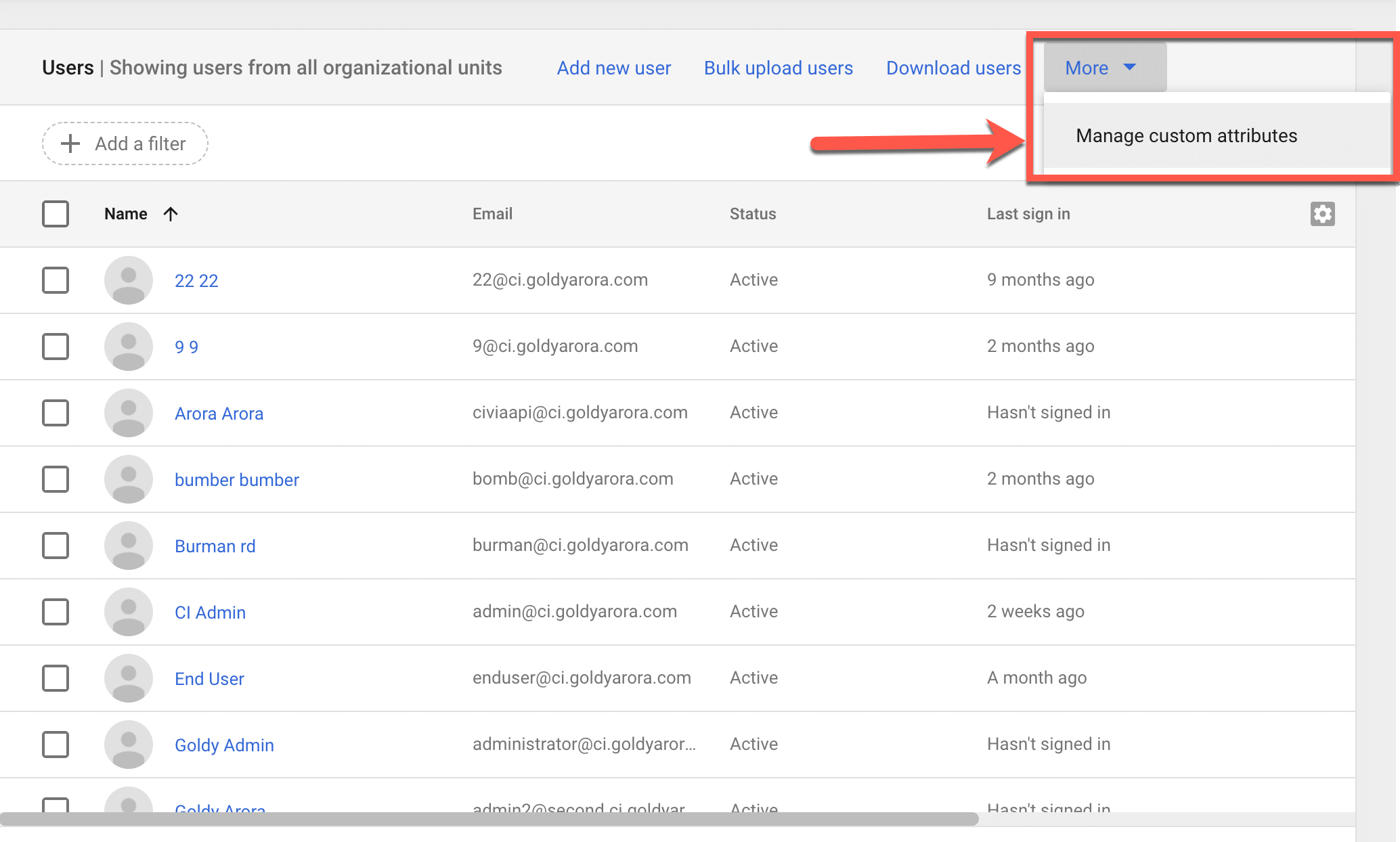
2. Create a custom attribute which will be looked up by GCPW for associating Google account with existing Windows AD profile.
(i) Category name should be “Enhanced desktop security“.
(ii) Custom field name should exactly be “AD accounts“.
(iii) Info type should be “Text“.
(iv) Visibility should be “Visible to User and Admin“.
(v) No. of values should be “Multi-value“.
(vi) Save changes

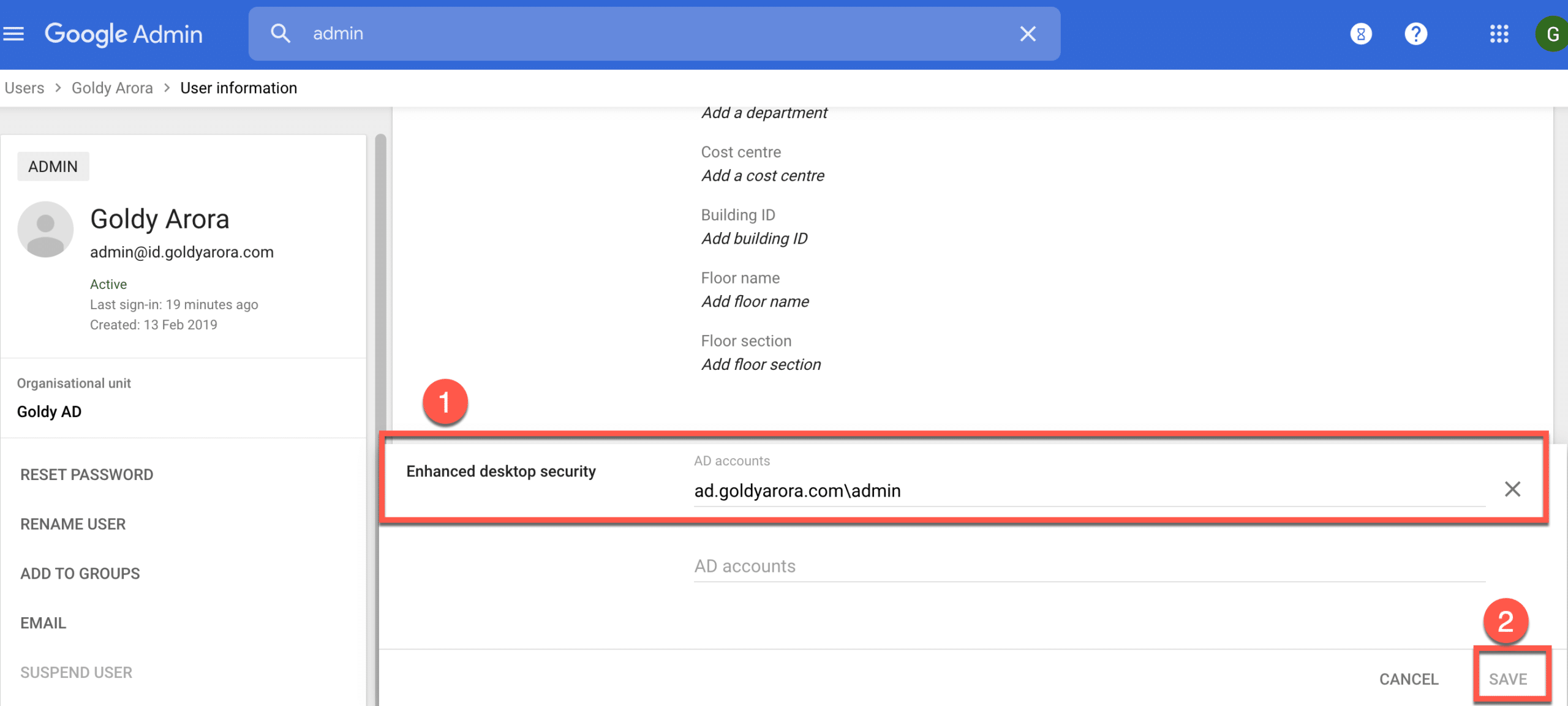
3. Populate the newly created custom attribute with the AD user sAMAccountName in format: domain\username.
For e.g my AD domain name is ad.goldyarora.com and my sAMAccountName is admin, so I would enter ad.goldyarora.com\admin as shown in the screenshot below.
Additional Step : If you want to associate existing Windows local profile with Google
In this post, I will configure Google to create a new windows profile with my users Google credentials, however if you want to rather associate your users Google profile with existing Windows local profile, then you should perform this additional setup.
1. Login to your Google Admin console –> go to Users –> click on Manage Custom Attributes

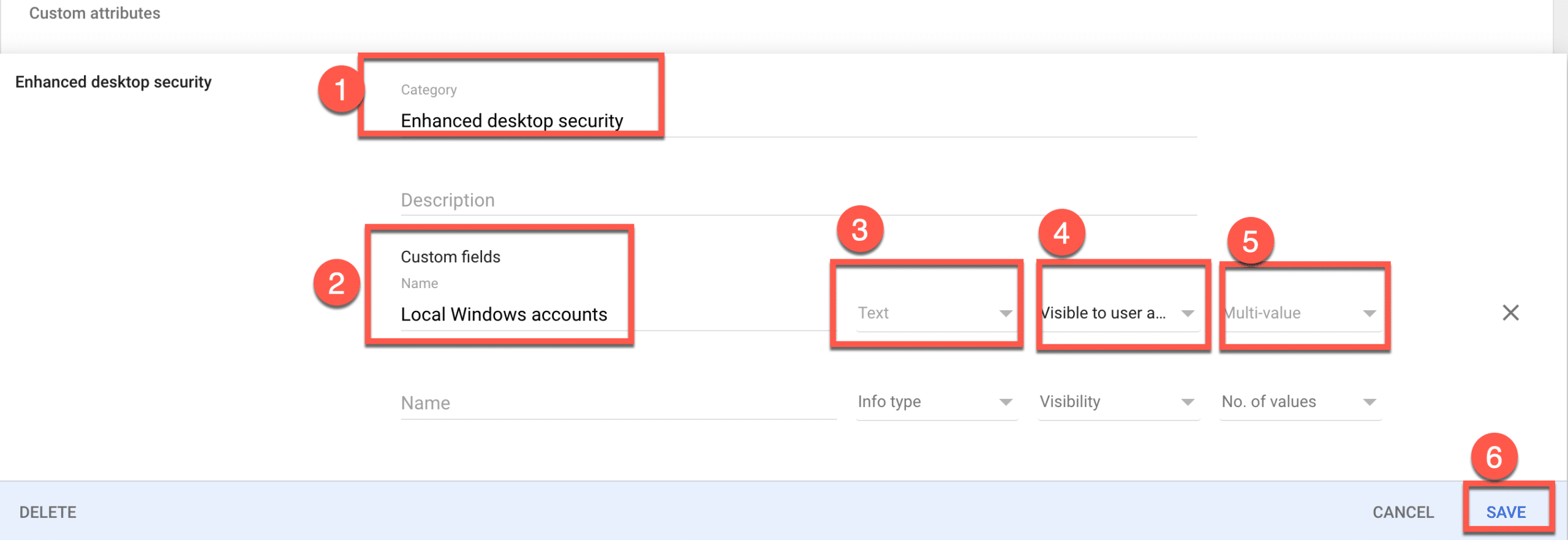
2. Create a custom attribute which will be looked up by GCPW for associating Google account with existing Windows local profile.
(i) Category name should be “Enhanced desktop security“.
(ii) Custom field name should exactly be “Local Windows accounts“.
(iii) Info type should be “Text“.
(iv) Visibility should be “Visible to User and Admin“.
(v) No. of values should be “Multi-value“.
(vi) Save changes
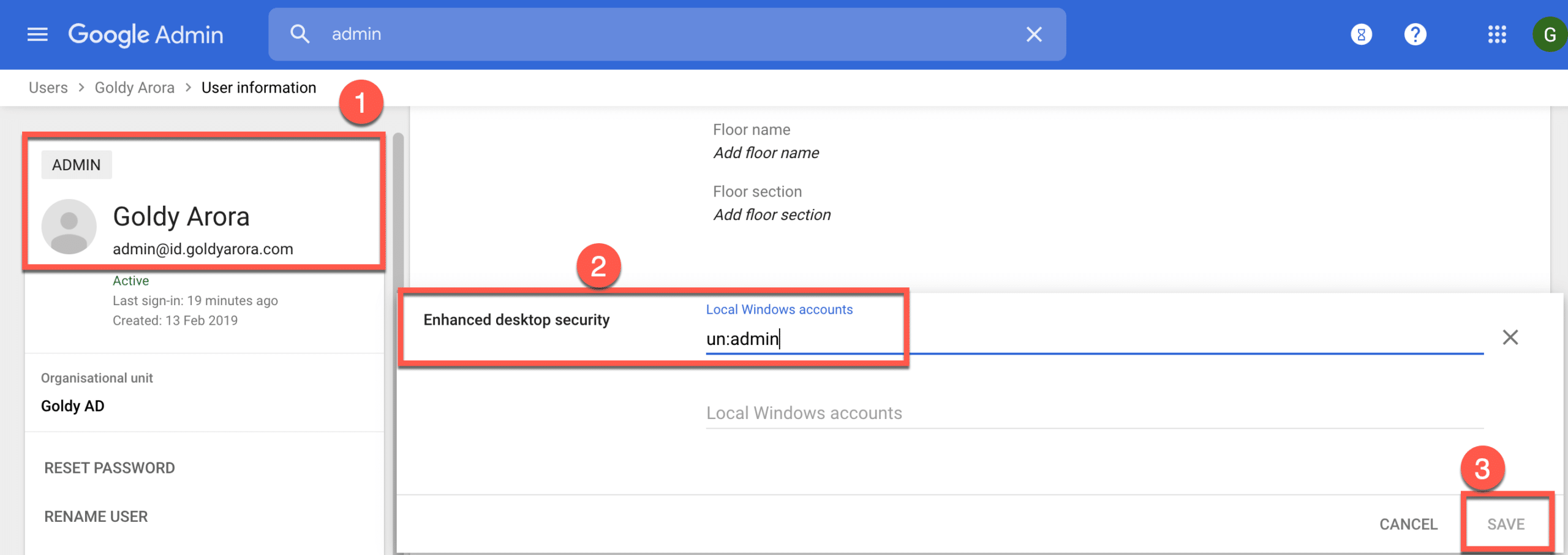
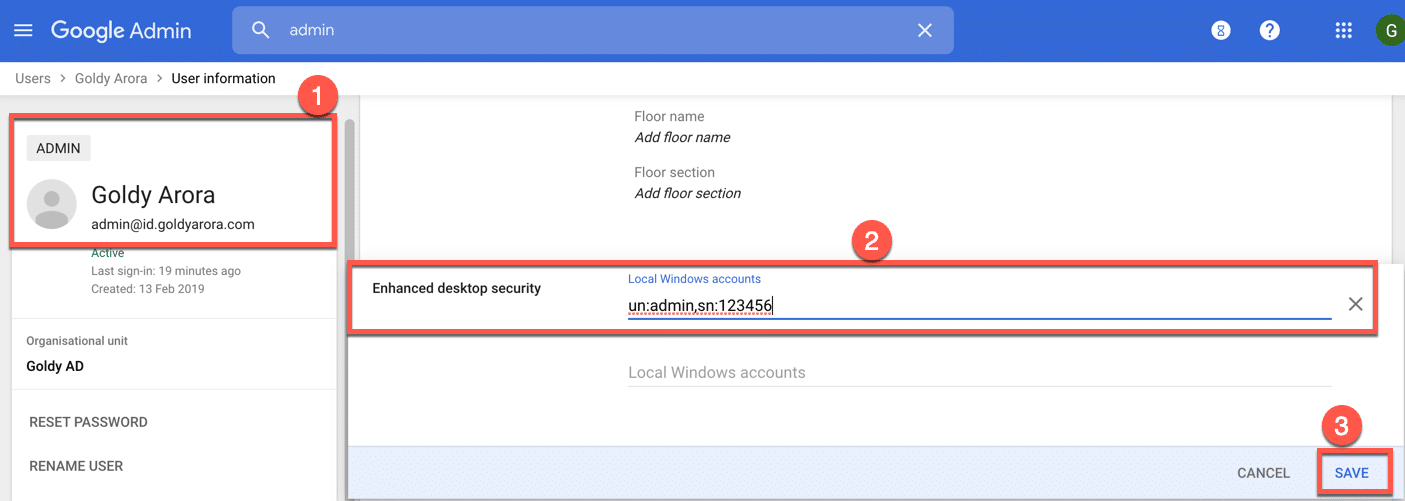
3. Populate this newly created custom attribute with local Windows user’s user name in the format un:username.
For e.g, my local windows profile name is admin, so i would enter un:admin as shown in the screenshot below.
3.1 If you want to restrict only one user to this respective device, then you should also write the device serial number along with the user name separated by comma (e.g un:admin, sn:123456) as shown in the screenshot below.
Step # 3 : Download & Install GCPW
Google Credential Provider for Windows Installation
You can either search Google for “Google Credential Provider for Windows” or click on this link https://tools.google.com/dlpage/gcpw
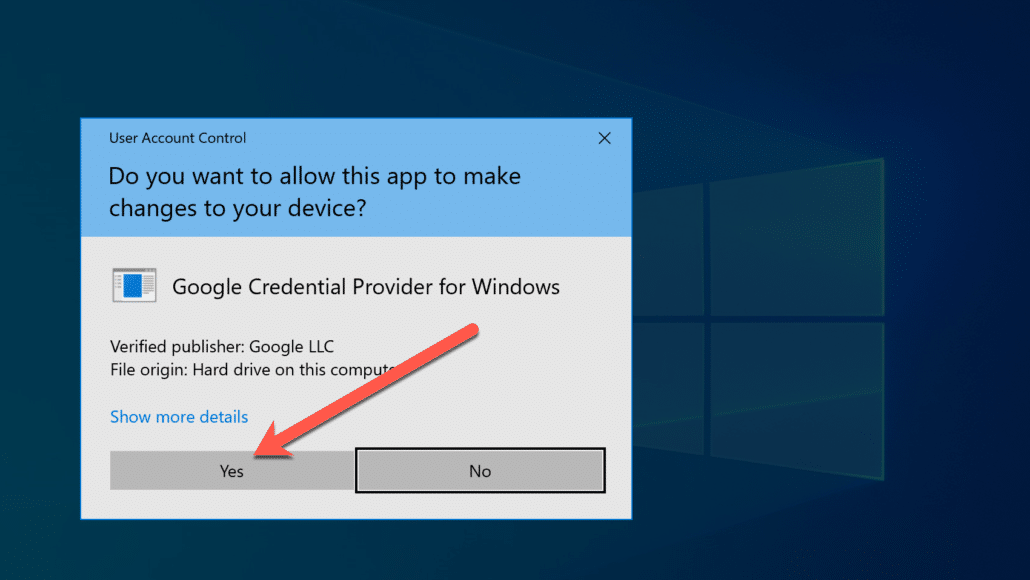
Download the version compatible with your system, and then run it with the local admin rights.

Allow the system to run the installation as shown in the screenshot below.
GCPW installation should start now and may take just a minute to finish.
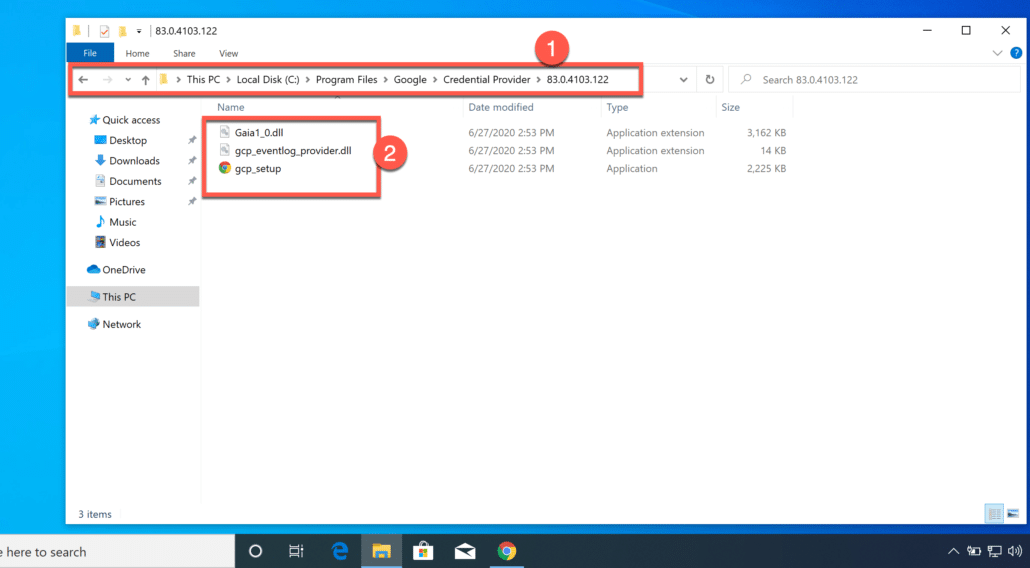
Once the installation is finished, you should-:
(1) Go the path shown in the screenshot below
(2) Ensure that it has created 3 files as shown below.
Step # 4 : Make Registry Changes
Available Registry Settings
Domains Allowed to Login
Description : This setting restricts users to login to Windows devices only if their email belongs to any of these domains.
Any user whom email does not belong to these domains will get an error when login to Windows via Google Workspace.
By default, no domains are allowed to sign in with GCPW.
Setting Type : Required
Configuration
Configuration Instructions
- In the Windows search box, enter regedit.
- In Registry Editor, go to HKEY_LOCAL_MACHINE\Software\Google
- Right-click the GCPW folder and click New
- String Value.
- For the name, enter domains_allowed_to_login.
- Double-click the name and, in the Value data box, enter a comma-separated list of allowed domain names. For example: id.goldyarora.com, goldyarora.com.
- Click OK.
If required, Please look at the screenshot based instructions later in this post where I perform this registry change.
Disable Device Enrollment
By default device enrollment is enabled, however if you want to use GCPW for authentication only, you may consider disabling device enrollment either here or in Google Workspace Admin Console.
Setting Type : Optional
Configuration Instructions
- In Registry Editor, right-click the GCPW folder and click New
- DWORD.
- For the name, enter enable_dm_enrollment.
- Double-click the name and, in the Value data box, enter 0. If you ever want to reset the key to allow automatic enrollment, change the value to 1.
- Click OK.
Session Validity
Enforce users to sign into Google Workspace online after their windows device is offline a set time
Default behavior : No value, online sign-in is not enforced.
Setting Type : Optional
Configuration Instructions
- In Registry Editor, right-click the GCPW folder and click New
- DWORD.
- For the name, enter validity_period_days.
- Double-click the name and, in the Value data box, enter the number of days between online GCPW sign-ins.
(e.g if you enter 7, the user needs to sign in online after their device is offline for 7 days, If you enter 0, the user needs to sign in online immediately after the device is disconnected from the internet). - Click OK.
Enable Multiple User Login
This setting let you define whether multiple users can login to a respective Windows device or not.
Default behavior : Multiple users are allowed to sign in to Windows device via their Google Workspace account.
Setting Type : Optional
Configuration Instructions
- In Registry Editor, right-click the GCPW folder and click New
- DWORD.
- For the name, enter enable_multi_user_login.
- Double-click the name and, in the Value data box, enter 0. If you ever want to reset the key to allow automatic multiple accounts on the device, change the value to 1.
- Click OK.
Windows Profile Association
This setting helps you define whether you want Google to create new Windows profile (default), or rather associate Windows local or AD profile with Google account.
Default behavior : Google does not associate existing Windows profile, and let users click on “Add Work Account” to create a new Windows profile via Google Workspace.
Setting Type : Optional
Configuration Instructions
- In Registry Editor, right-click the GCPW folder and click New
- Key.
- Name the key Users.
- Right-click the Users folder and click New
- Key.
- Name the key the user’s Windows account SID (security identifier).
- Right-click the SID folder and click New
- String Value.
- For the name, enter email.
- Double-click the name and, in the Value data box, enter the work account you want to associate with the user’s local Windows account. Use the user’s full email address, such as user@id.goldyarora.com.
- Click OK.
Make Registry Changes
Though you may configure the optional registry changes as well if required, however I would configure only the required one for this demonstration.
Go to your Windows search and type regedit as shown below.
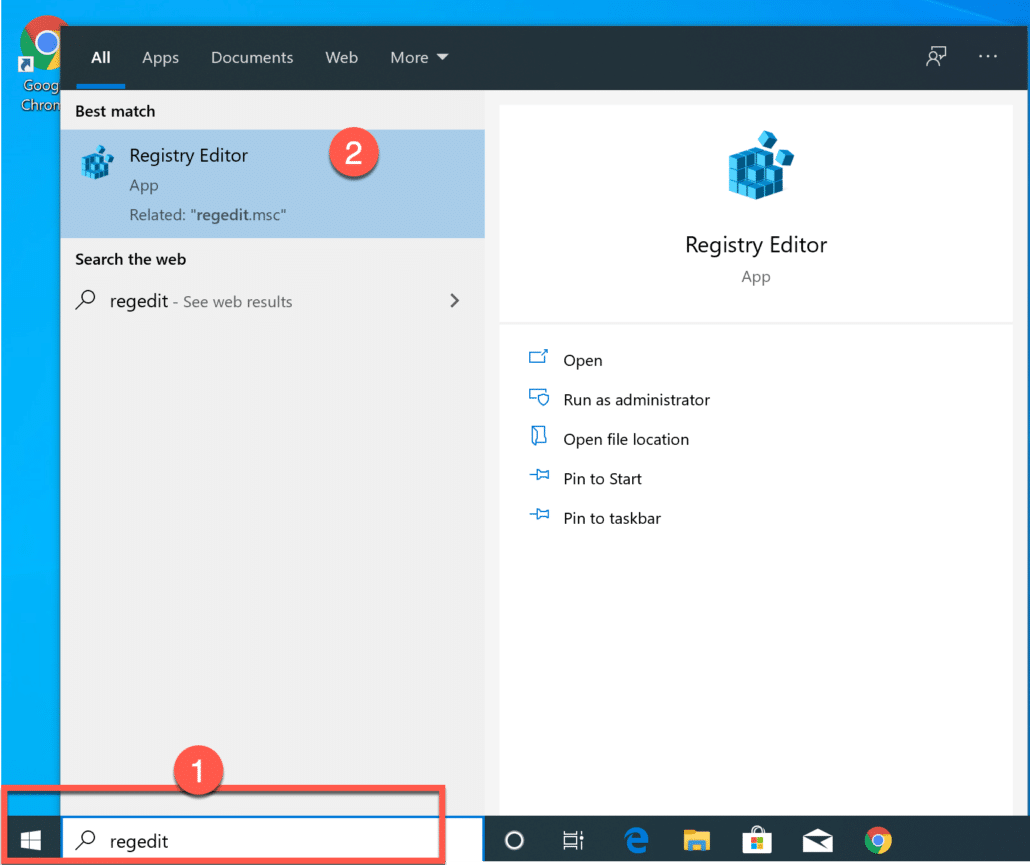
1. Go to HKEY_LOCAL_MACHINE
2. Go to GCPW.
3. Right click and click on New.
4. Click on “String Value” and name it domains_allowed_to_login
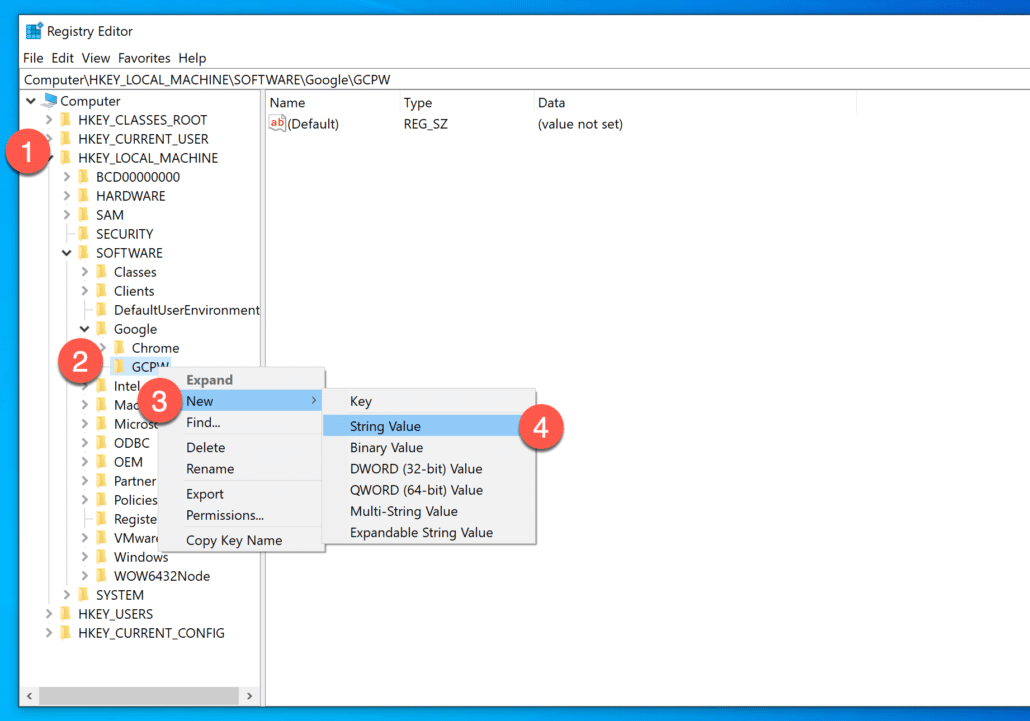
Now, right click on domains_allowed_to_login and enter the comma separated Google Workspace or Google Cloud Identity domain names which you want to allow for login in to this Windows device.
I want my users to login from any of my three Google Workspace domains, so i have entered them separated by comma, however if you have only domain, simply enter it here.
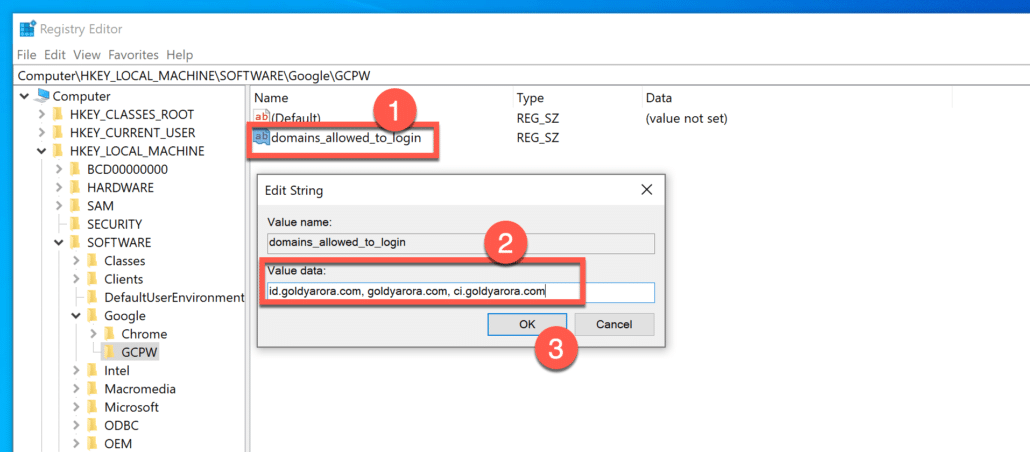
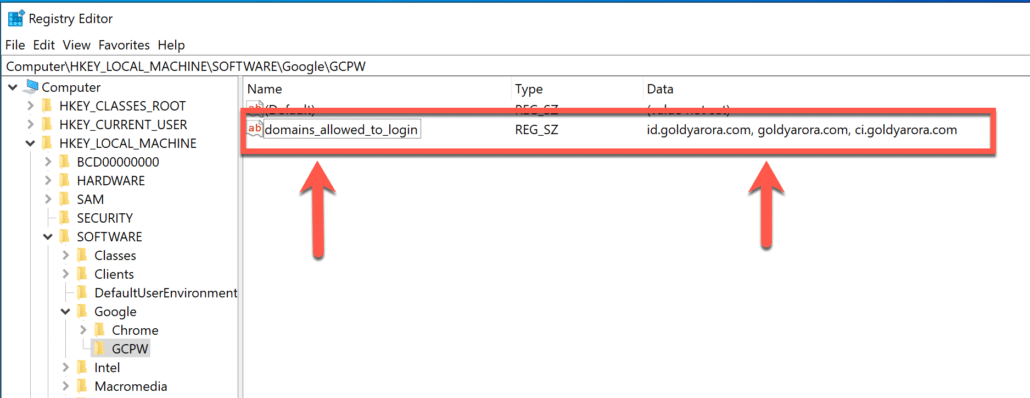
Your completed domains_allowed_to_login entry should look like the screenshot below.
Additional Steps - Depending on your profile strategy.
If you decided to rather associate your existing Windows local or Active directory profile with Google account, then you would need to make an additional registry setting, which will let GCPW look for your custom attribute that you created in Google directory.
You should follow either of the following step only if want to associate users Google account with local or AD windows profile.
Registry Change : If you want to associate existing Windows profile with Google
If you want to associate users’ existing Windows profile with their Google Workspace or Google Cloud Identity account, then create this registry key as follows :
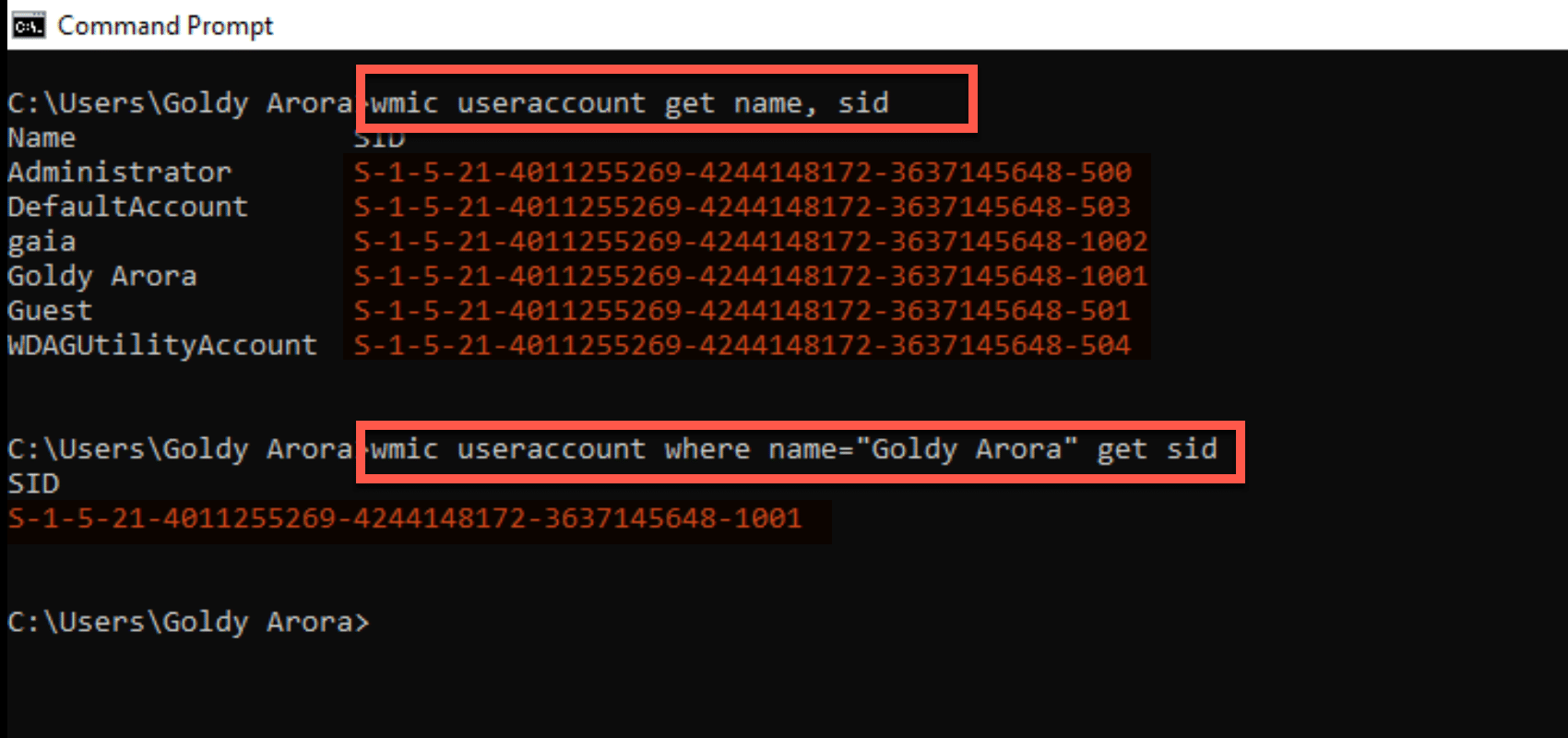
Before we create the registry key, we’ll need user’s security identifier (e.g SID), you can use following command in CMD on the respective device to find user’s SID.
Commands :
If you don’t know the user name : wmic useraccount get name, sid
If you know the user name : wmic useraccount where name = “Your User Name” get sid
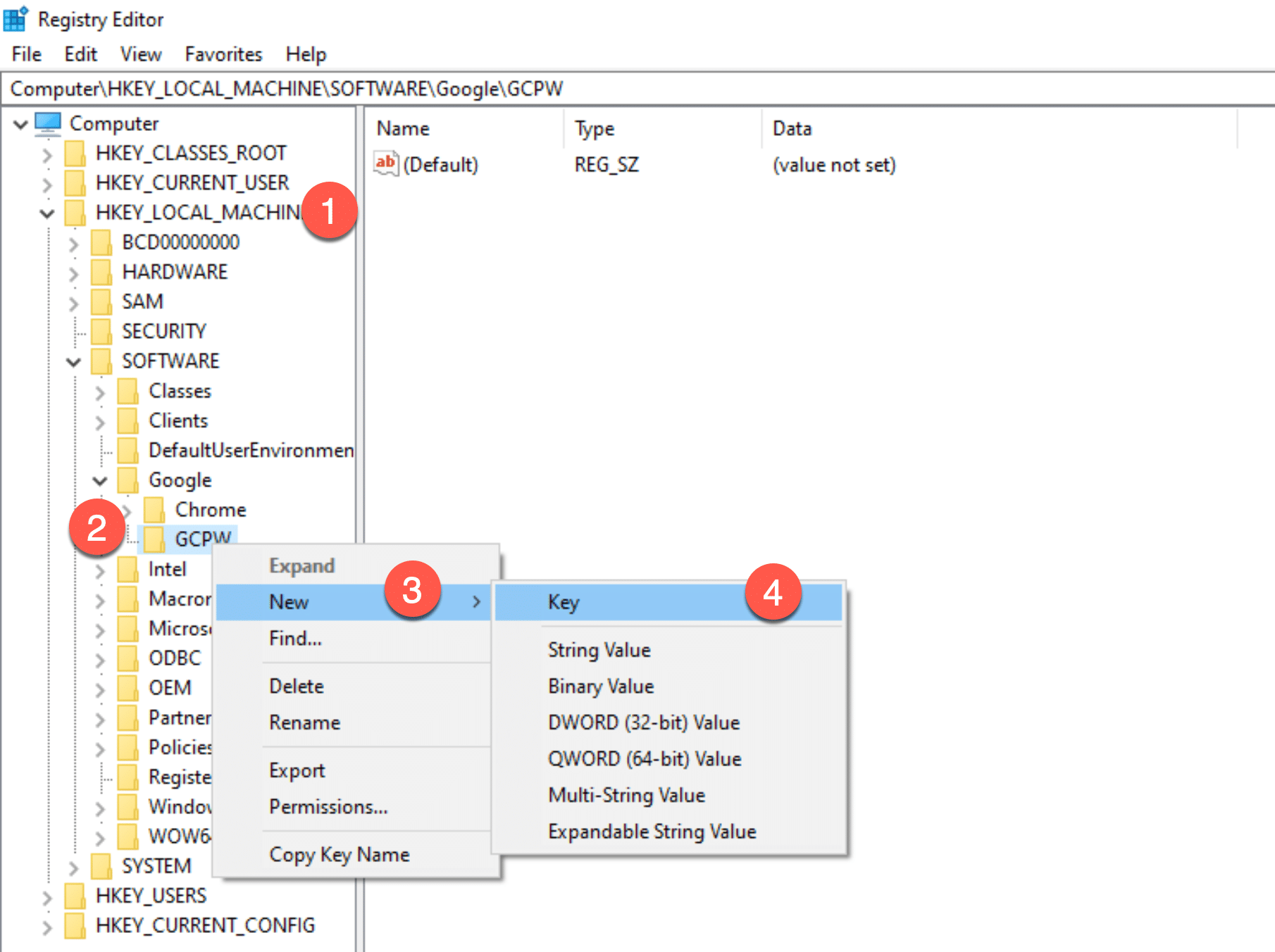
Go to registry settings (regedit) –> HKEY_LOCAL_MACHINE –> Software –> right click on GCPW and create a new Key called “Users”
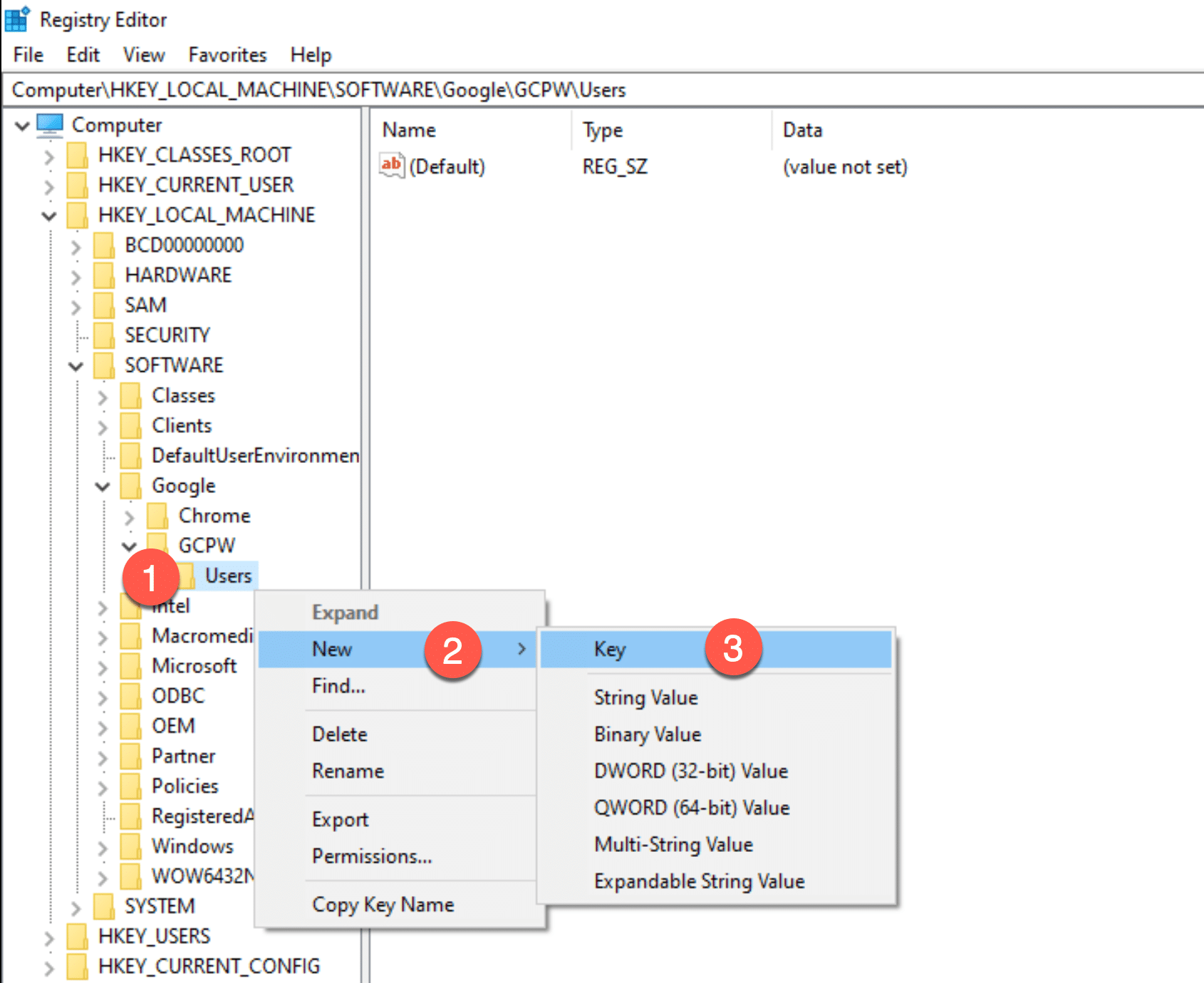
Now, right click on the newly created Users folder to create a new key with the SID you got above.
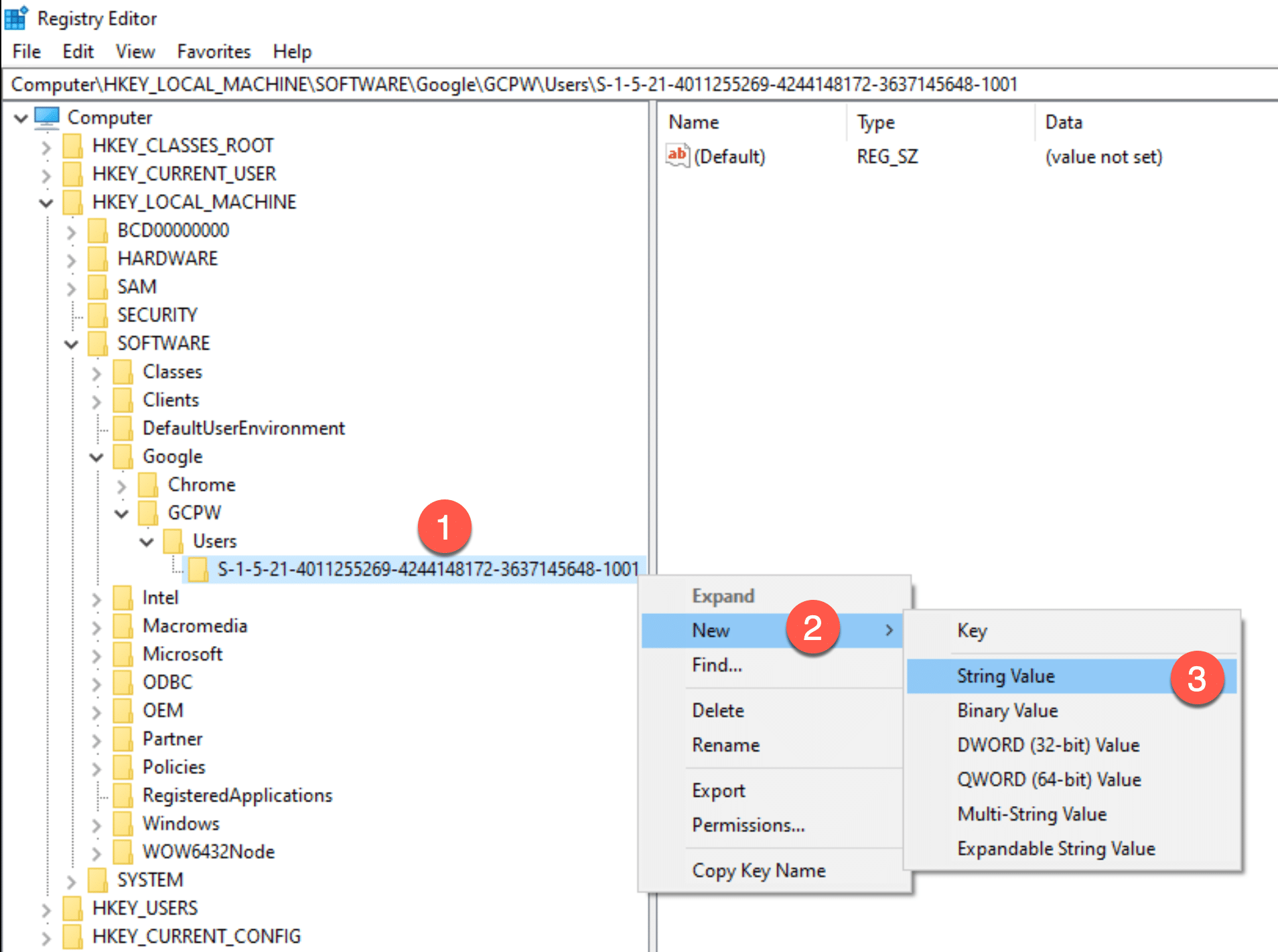
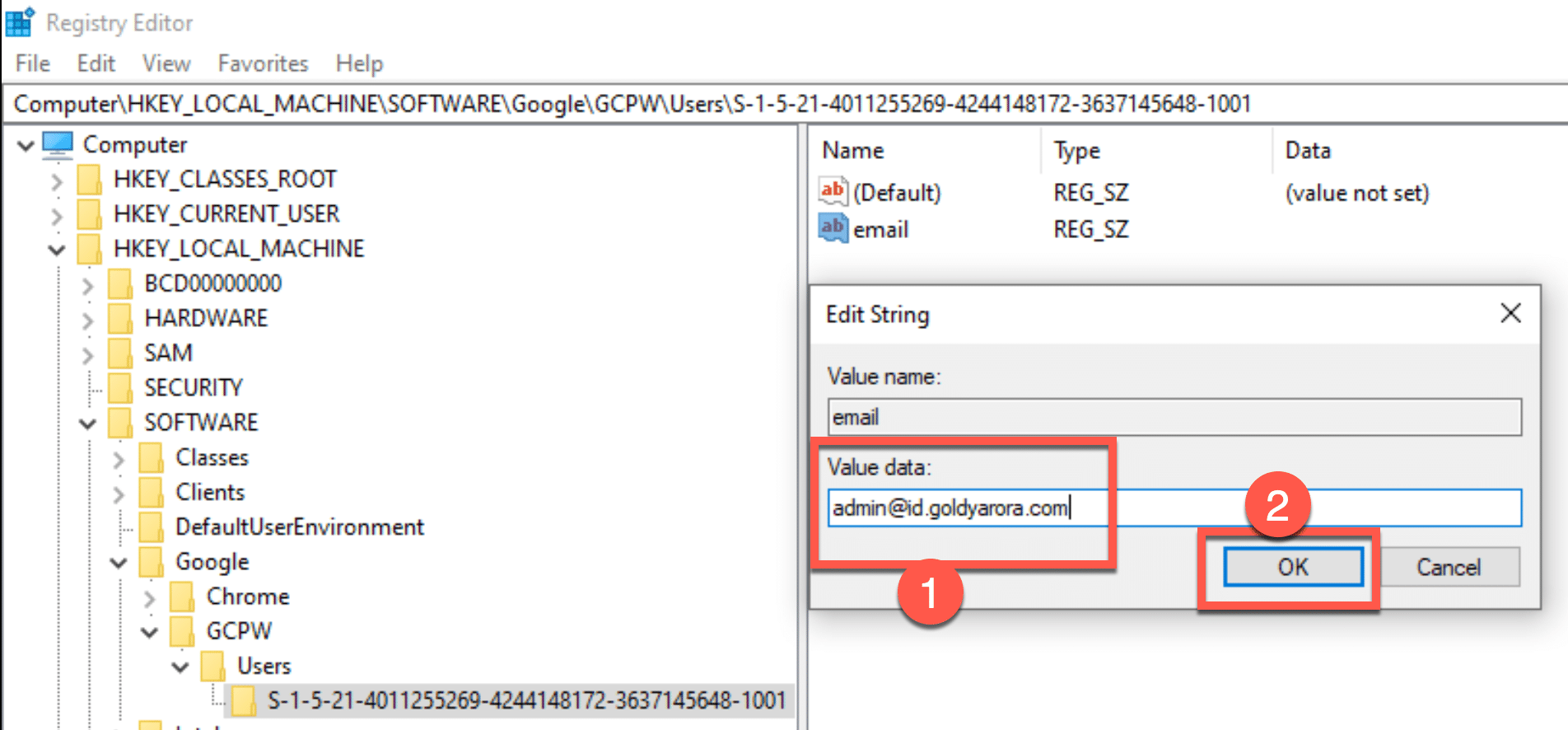
You should now right click on the SID folder, and create a new String Value called “email” as shown in the screenshot below.
You should now right click to modify the email value.

Enter your Google Workspace or Google Cloud Identity user’s full email address here as shown below.
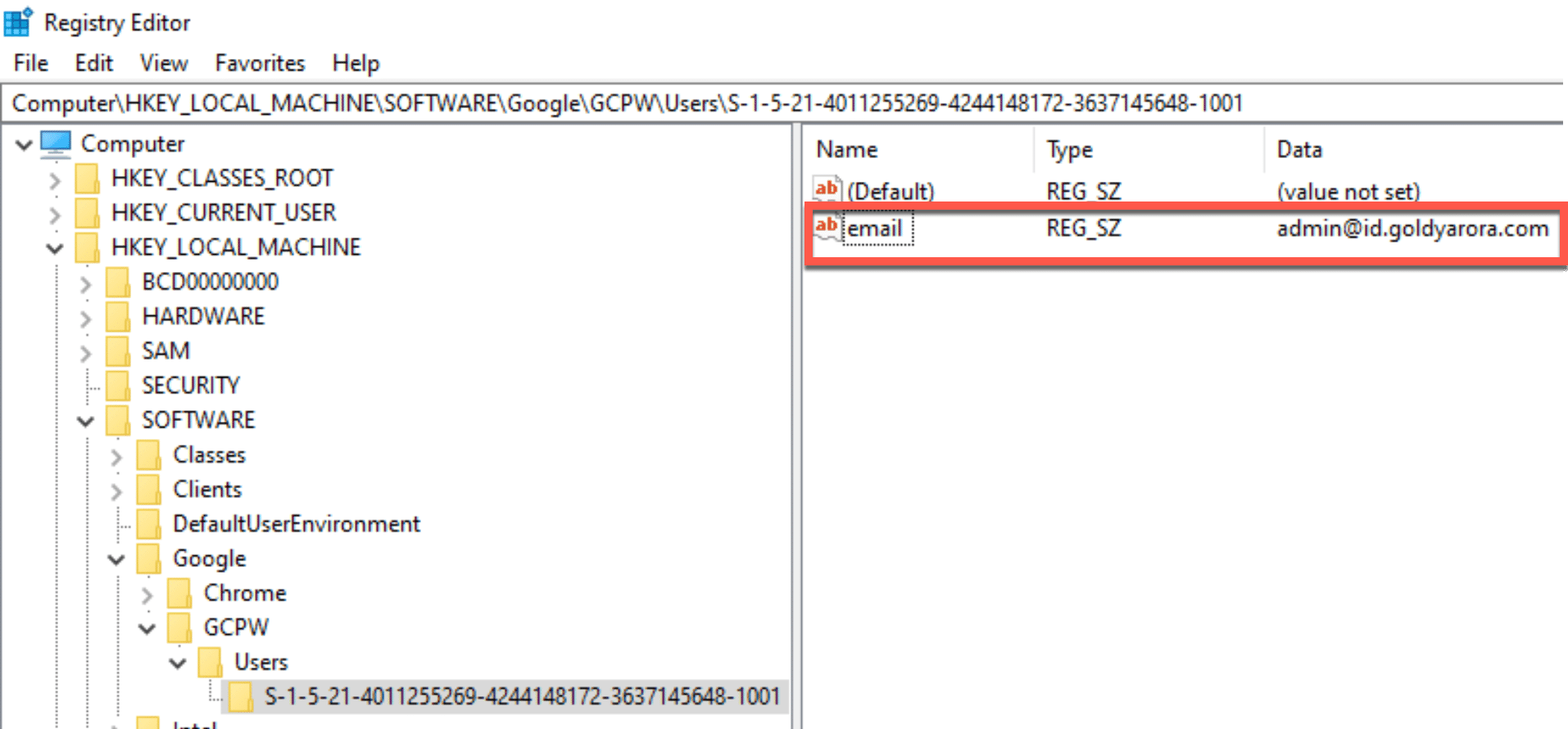
Your entry would look like the screenshot below.
Step # 5 : Configuration Testing
Now sign out from your Windows device, and let’s start testing login to it via any of the Google Workspace domains we allowed above.
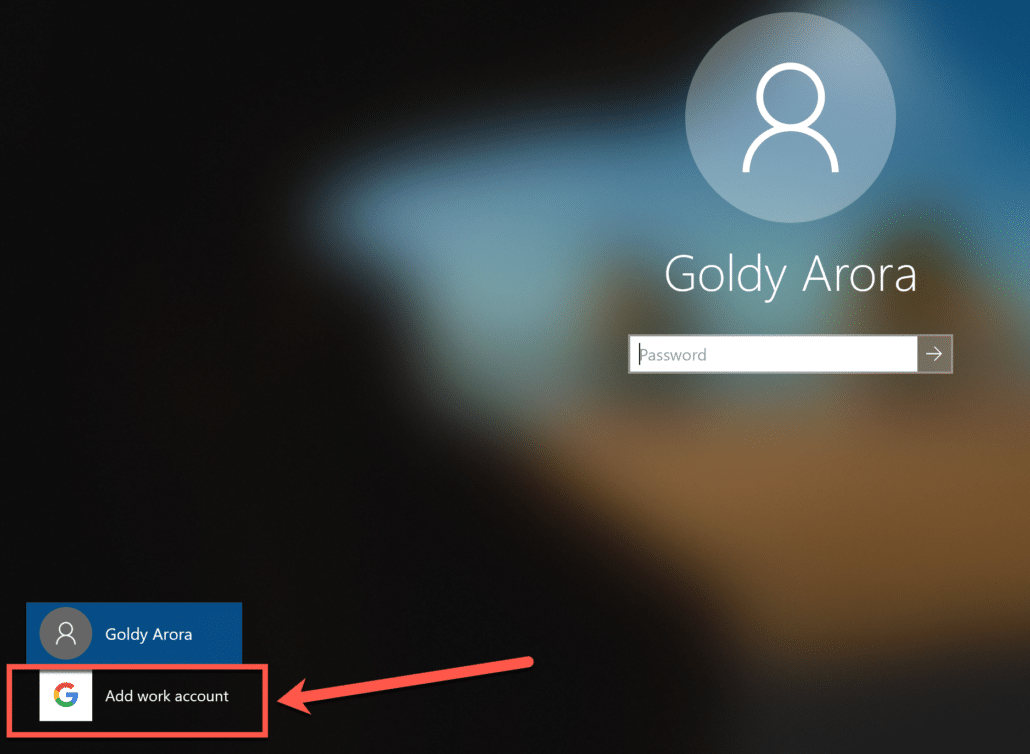
You would notice a new “Add Work Account” option with Google logo as shown in the screenshot below, click on it.
Note : If your admin has setup to associate existing Windows profile with Google account, then you should be able to rather click on your existing Windows profile to login via Google.
After you click on Add Work Account, you would see a Google screen suggesting you to sign in with your work account as you see below. Click on the arrow to start login via Google process.

Enter your Google Workspace or Google Cloud Identity email address.
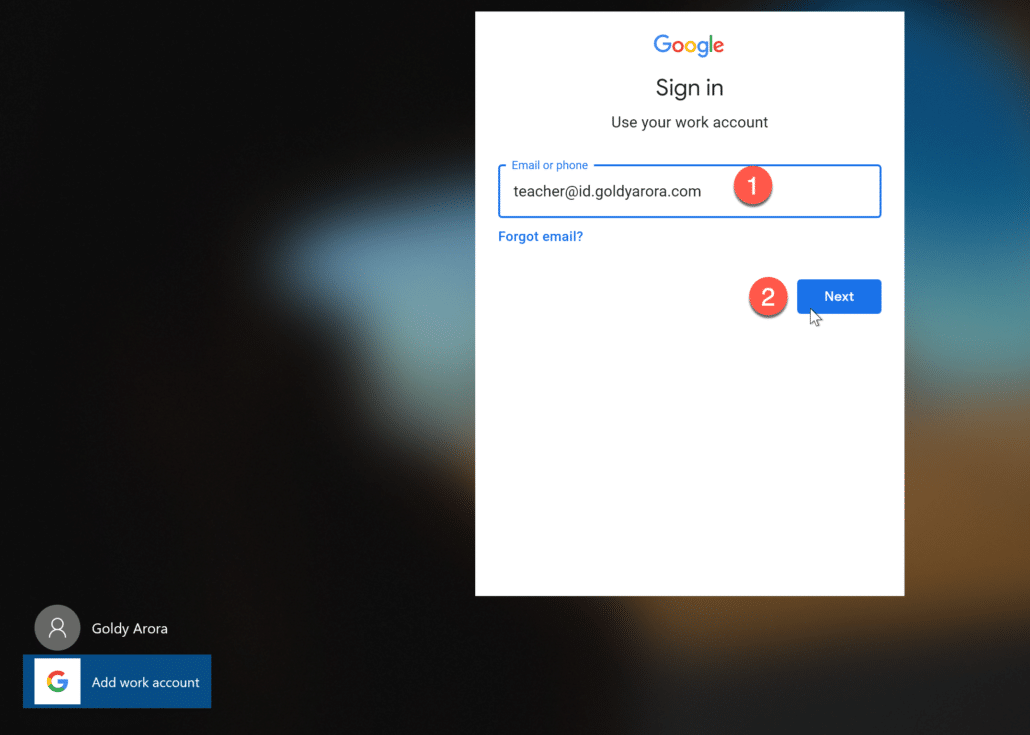
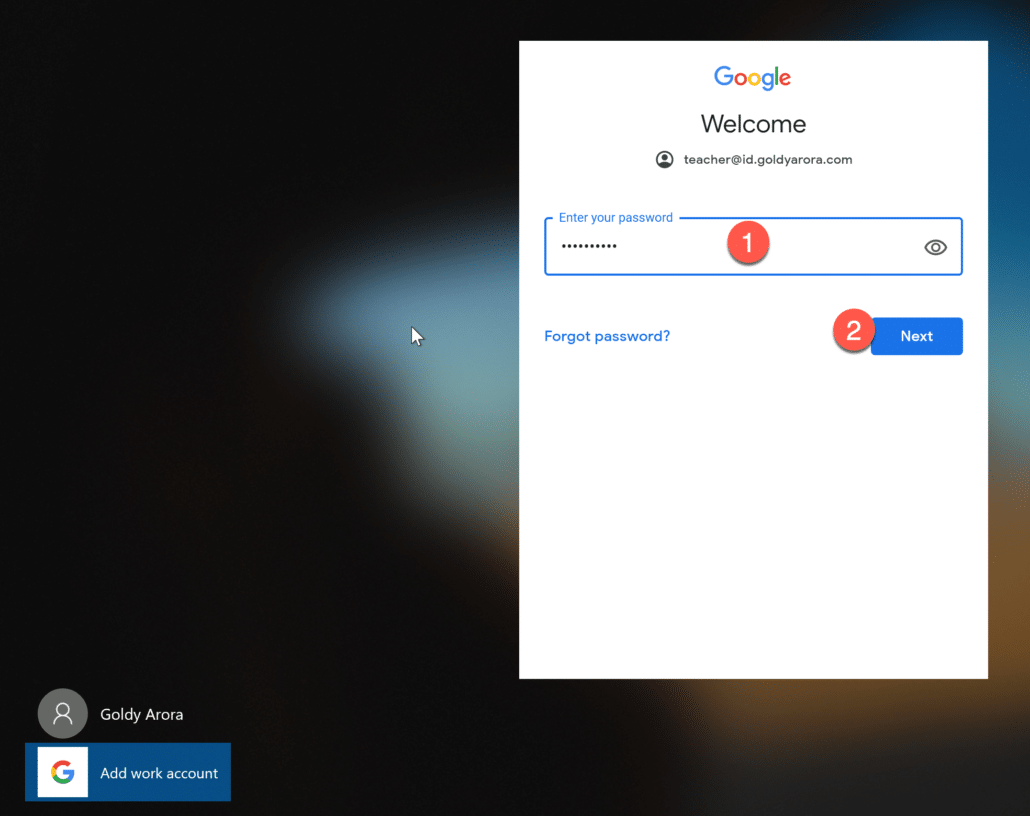
Enter your Google Workspace or Google Cloud Identity account’s password.
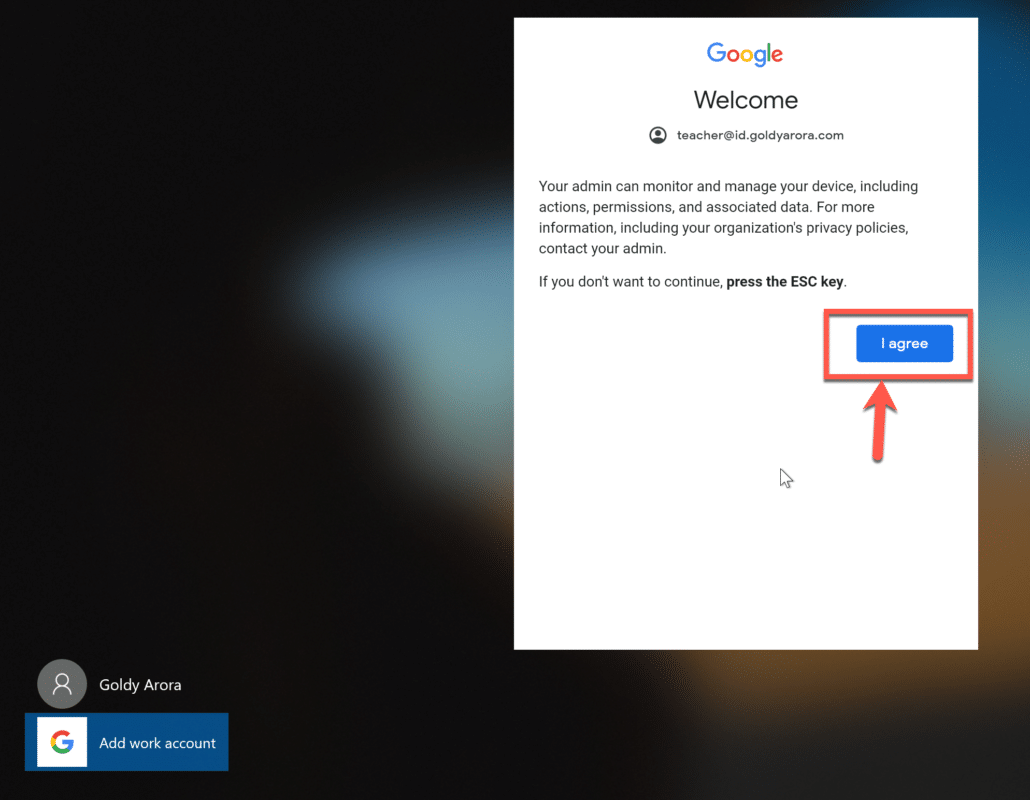
As this is our first login, Google would inform us that our Google Workspace admin can monitor and mange this device. Click on “I agree” to continue with the process.
Your new windows profile is now getting ready, it may take a few minutes.
Note -: If you associated your existing local or AD windows profile with Google Workspace, then new profile would not be created, and you would rather straight away login to your Windows.
Your new Windows profile has been created via Google Workspace, and is now ready for you.
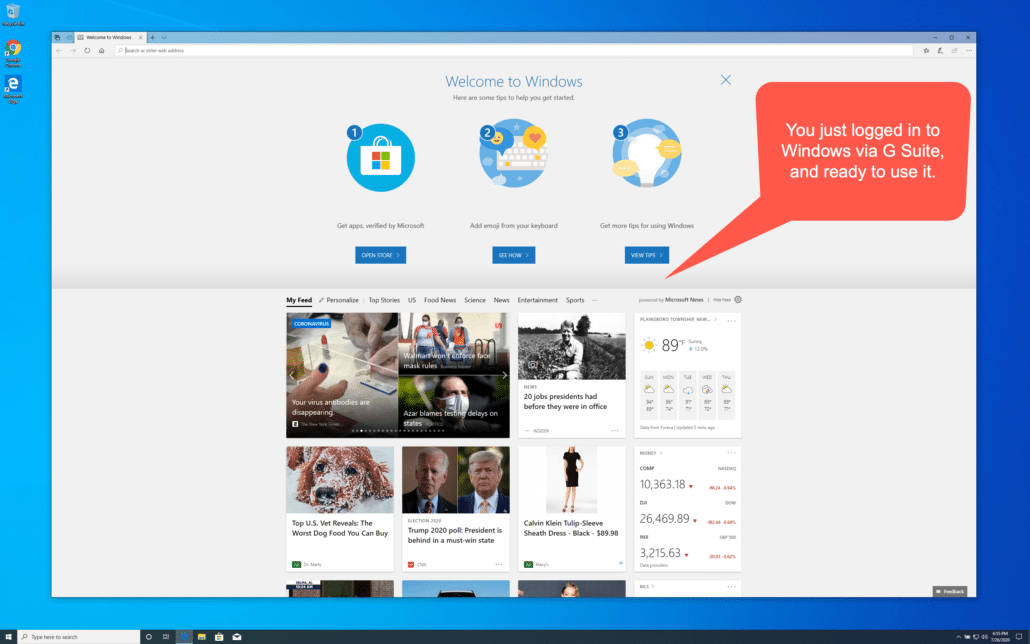
However, you would notice that user can neither use camera, nor change its setting due to the custom setting we pushed earlier.
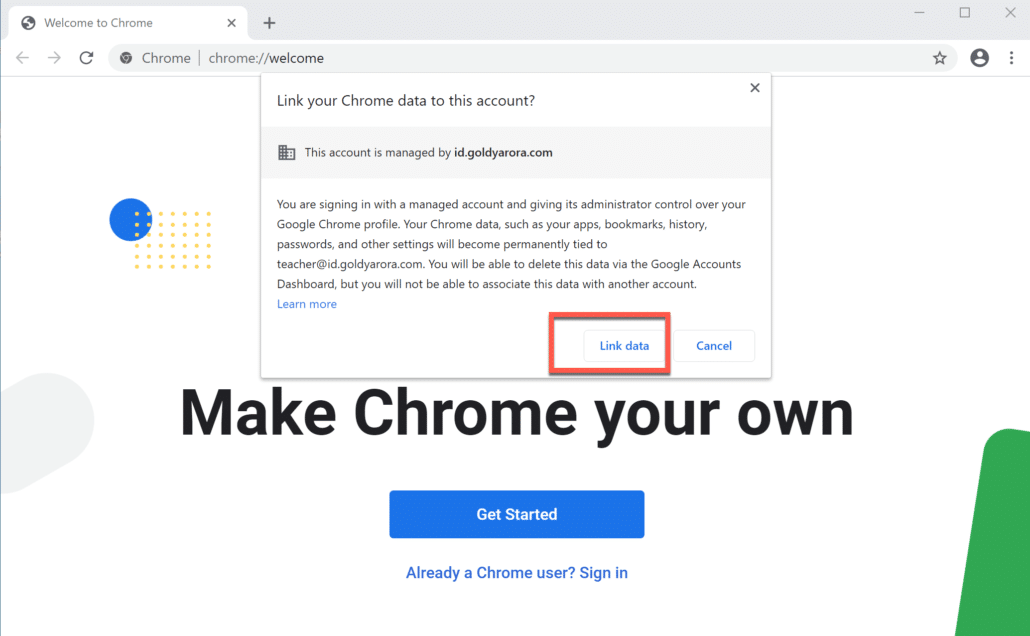
Sign in to Google Workspace & assigned SAML Applications
When you login to Windows via your Google Workspace or Google Cloud Identity credentials, a session is established which lets you login to assigned Google Workspace and SAML applications.
When you launch Google Chrome after login to Windows via Google Workspace, you would be asked to link your profile/data to your Google Workspace organization.
Now you can go to any Google Workspace application url (e.g drive.google.com, mail.google.com etc), or to your Google Workspace dashboard at gsuite.google.com/dashboard where you’ll see all the applications assigned to you.
Click on any of these application to login without a need to enter credentials again.
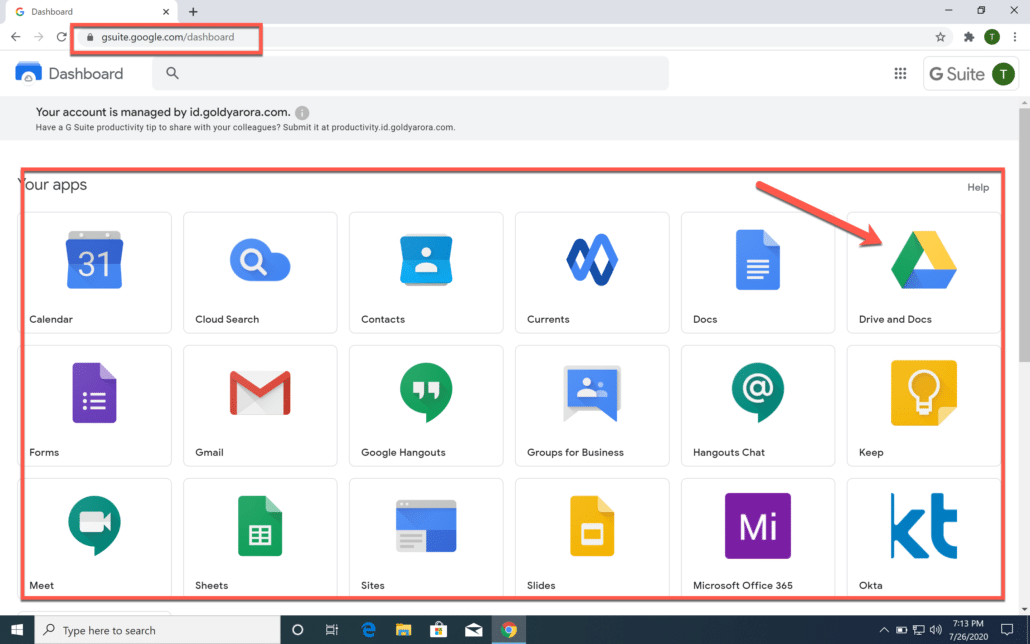
You should be logged into the application via an active session as shown in the screenshot below.
Device Enrollment Reporting
When your users sign in to Windows via Google Workspace, they get enroll in Google Credential Provider for Windows, GCPW (and also in Enhanced Desktop Security if you have automatic enrollment enabled along with supported Google Workspace or Cloud Identity subscription).
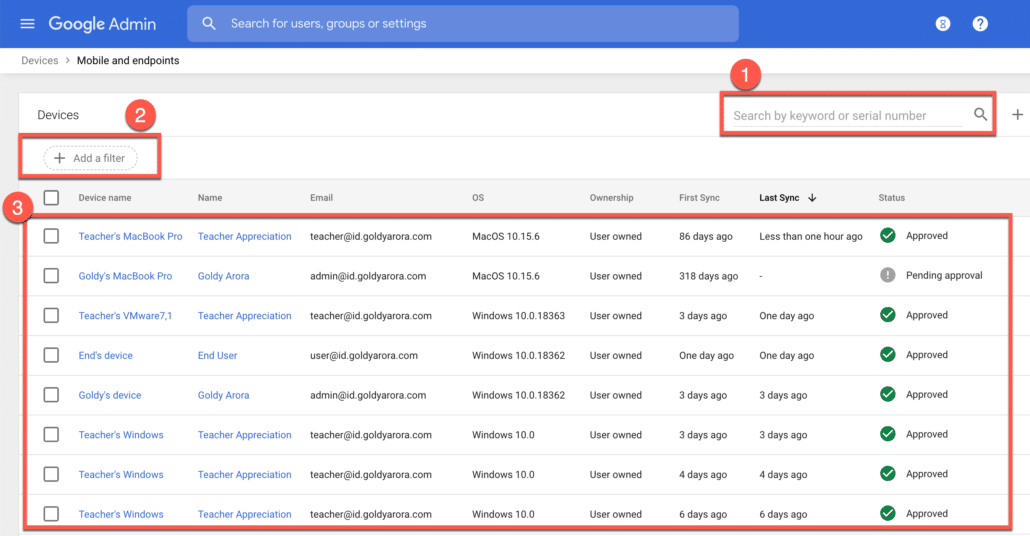
To view the devices inventory, go to your Google Workspace admin console (admin.google.com) and click on devices.

Now click on Endpoints as shown in the screenshot below.

Here you can either search for the Windows device by user name or other properties, or add a filter to view devices based on your criteria (e.g OS matches Windows AND status = Pending Approval).
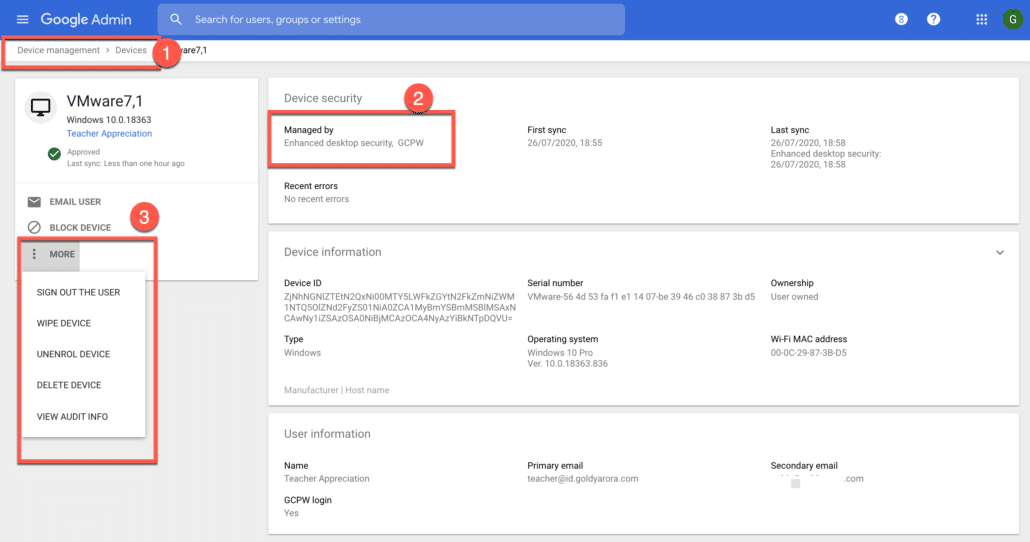
Here you should be able to perform a few operations including-:
- Search and filter your devices based on criteria (e.g OS, user, last sync, serial no. etc).
- Look at device information like user email, last sync, OS version etc.
- Sign out the user, wipe device (factory reset), unenroll, and delete the device.
Troubleshooting & FAQs
I AM GETTING AN ERROR "YOU CAN ONLY SIGN IN WITH AN EMAIL ADDRESS THAT ENDS WITH FOLLOWING...

This error indicates you are trying to sign in with the email domain that is not included in Domains Allowed to Login registry setting.
Solution : Either try the email address on the allowed domain, or add the required domain to the registry key as shown above in the change registry settings section.
"YOUR ADMINISTRATOR DOESN’T ALLOW YOU TO SIGN IN WITH THIS ACCOUNT. TRY A DIFFERENT ACCOUNT."
This error indicates Admin has not yet configured Domains Allowed to Login registry setting.
Solution : Add the required domain/s in the Domains Allowed to Login registry key.
"THE WINDOWS PASSWORD IS INCORRECT. TRY AGAIN."
This error indicates that the user’s Google and Windows passwords are not in sync, This message appears when user enters the wrong Windows password.
Solution : Sync Google and Windows password.
"CAN'T OPEN THE GOOGLE SIGN-IN SCREEN BECAUSE THERE'S AN ISSUE WITH THE CHROME INSTALLATION ON THIS DEVICE. CONTACT YOUR ADMINISTRATOR. "
As per Google,
To fix this issue, you can install or reinstall the Chrome browser on the user’s device.
However, in my experience, this error also occurs when you install GCPW on a non supported Windows version (e.g Windows Server 2016).
Related Posts
....

